Things You Need To Know About Celebrities Twitter Hack

The FBI is now also busy with the spectacular Twitter hack, in which around 130 celebrity accounts were attacked and misused for a Bitcoin scam. Now Twitter has also added more details and published further details about the attack.
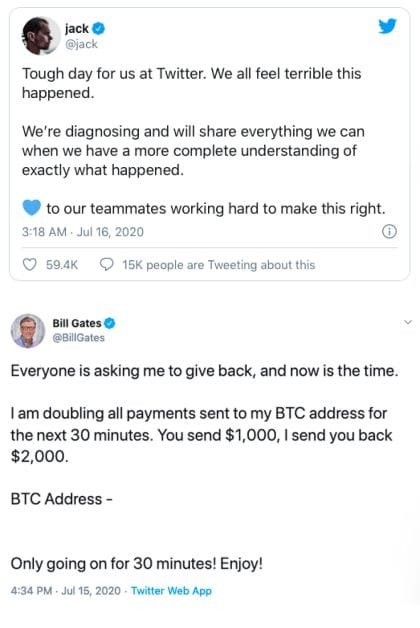
In the night from Wednesday to Thursday, a previously unknown group had tried to take over about 130 Twitter accounts from well-known personalities and asked via tweets to transfer $1,000 to Bitcoin. It was stipulated that the celebrities wanted to double the money, meaning that anyone who sent $1,000 would get $2,000 back. Accounts from EX-US President Barack Obama, Microsoft founder Bill Gates, Amazon boss Jeff Bezos and company accounts from Apple and Uber were used for this. As far as is known, the Bitcoin calls from 45 accounts were sent.
Small loot – $121,000 stolen
According to CNBC’s initial research, around 400 transactions were carried out within a very short period of time, meaning that the fraudsters landed $121,000 before the spook could be ended. The money is gone, the cheated users are likely to remain seated on their damage. The FBI has meanwhile started investigations to clarify the background – but the money is no longer available. The FBI now wants to clarify primarily how it could happen that several security measures could be circumvented.
Because, as it was said shortly after the hack became known, unknowns had escaped the favor of some Twitter employees. Others suspected that Twitter employees had voluntarily participated in the scam, but this has not yet been confirmed.
Many guesses, few facts
Finally, the fraudsters were able to infiltrate employee accounts to use internal tools that made the scam possible. In addition, another theory has now become known via Mirror that the unknowns reset the passwords of the hacked accounts and were able to initiate authentication because they had hijacked the phone numbers associated with the Twitter accounts via so-called SIM swapping.
However, the investigations are still in a stage that is much too early to have any reliable knowledge. It should be interesting for the Otto Normal user on Twitter, however, that the company deals with new information very transparently. In a detailed blog post, Twitter has now picked up all sorts of questions that had arisen in connection with the Bitcoin fraud. The company also disagrees with security expert Brian Krebs, who claims in his blog that “attackers had the opportunity to read the direct messages of all Twitter users.” According to Twitter, there is no indication of this.
Twitter has now published these facts and assumptions:
- Twitter suspects that the attackers have targeted employees through social engineering.
- The attackers successfully manipulated a small number of employees and used their credentials to access Twitter’s internal systems, including penetration of the two-factor protection mechanisms – so there is no question of SIM swapping.
- 130 Twitter accounts were targeted, with 45 of these accounts the attackers could initiate a password reset, log into the account, and send tweets.
- Attackers may have tried to sell some accounts.
- The Twitter intervention team secured affected accounts and revoked access to the internal systems to prevent the attackers from continuing to access the systems or individual accounts.
- Preventive measures were also taken to prevent further tweets from being sent and passwords changed.
Twitter is now working with law enforcement to investigate the incident. According to the Twitter blog post, the unknowns had no access to private information from other accounts. The affected users of the 130 accounts were informed. According to Twitter, the attackers were unable to view passwords, as they were not saved in plain text or available via the tools used in the attack. However, the attackers were able to see personal information such as email addresses and phone numbers. The internal forensic investigations of the activities have not yet been completed.
Digital marketing enthusiast and industry professional in Digital technologies, Technology News, Mobile phones, software, gadgets with vast experience in the tech industry, I have a keen interest in technology, News breaking.