Gigabyte Motherboards Had Firmware Backdoor
PC users probably have millions of motherboards installed, which actually invite attackers with a backdoor to gain access to the system. The vulnerability was largely deliberately installed by the manufacturer.
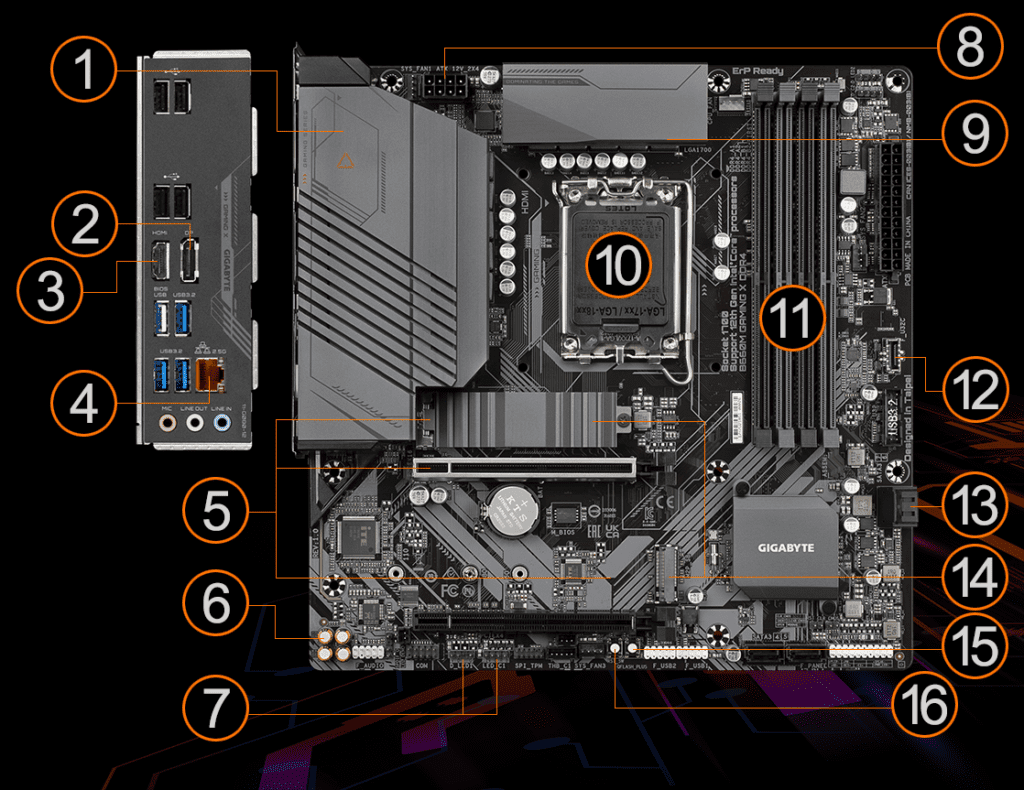
According to a report by the US magazine Wired, the motherboards from the manufacturer Gigabyte are affected. Their UEFI firmware contains a small tool that is actually supposed to check that the code is up-to-date and, if necessary, to pick up and install updates, according to analyzes by security researchers at Eclypsium, a company that specializes in firmware security.
Accordingly, the supposedly harmless tool is implemented insecurely. That opens the door to attackers. “If you own one of these computers, what you have to worry about is that it’s basically taking something off the Internet and running it without you having to do anything – without doing it in a secure way,” said John Loucaides, Eclypsium’s chief executive officer and research is responsible.
In its blog post about the investigation, Eclypsium lists 271 models of gigabyte motherboards that the researchers say are affected. Windows users can easily find out whether there is a corresponding component in their own PC: they simply click on “Start” and then on “System information”, where the relevant data is then displayed.
Patch is in progress
Eclypsium researchers said they found the hidden firmware mechanism by scanning customers’ computers for firmware-based malicious code. Because the UEFI is always the target of attackers. In 2018, hackers working for the Russian military intelligence agency GRU were caught installing firmware-based anti-theft software LoJack on victims’ computers as a spying tactic. Chinese state-funded hackers were caught two years later installing a firmware-based spy tool on the computers of diplomats and NGO workers in Africa, Asia, and Europe.
Eclypsium researchers were surprised that their automatic detection scans hit the update mechanism. According to the following analyses, this was probably right. The security researchers are currently working with Gigabyte to seal the insecure components of the updater, so appropriate patches should be made available here soon. Until then, we recommend disabling “APP Center Download & Install” in the UEFI and setting a password to prevent unauthorized manipulation of these settings.
Digital marketing enthusiast and industry professional in Digital technologies, Technology News, Mobile phones, software, gadgets with vast experience in the tech industry, I have a keen interest in technology, News breaking.