Email Vulnerability in Microsoft Office Can Be Removed
Emails are a gateway to all sorts of security vulnerabilities in many different forms. In most cases, malware is sent as an attachment or a link that leads to a hidden exploit. Currently, however, there is a vulnerability in the mail view of Microsoft’s Office suite, which is used by most Windows users through Outlook and does not require user interaction.
Short intervention
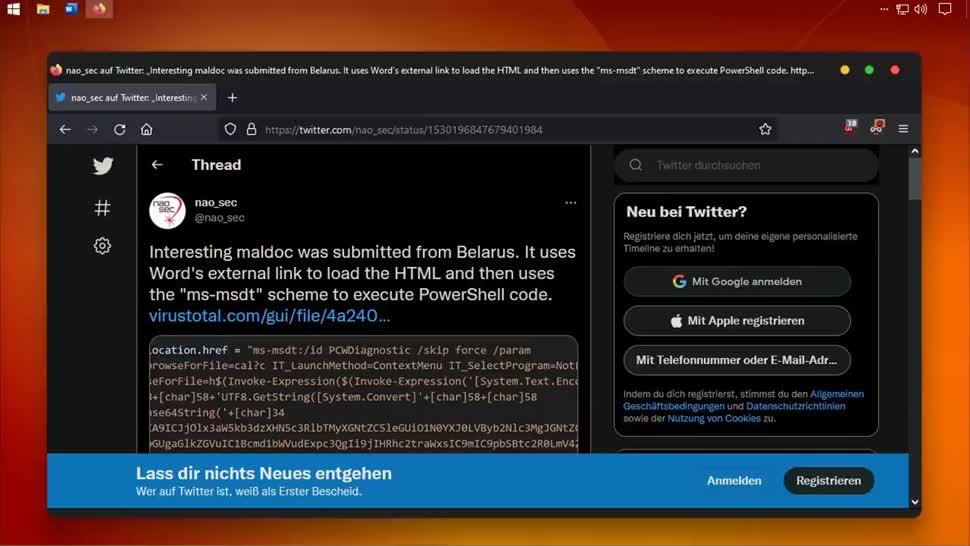
As colleagues from semper video can demonstrate, it is sufficient for the attacker to embed the malicious code into the HTML code of an email. From there, it can be passed directly to the shell via the protocol handler ms-msdt, which is part of the Microsoft Diagnostic Tool, where it runs with all kinds of privileges. However, the problem can be solved quickly with a small fix.
All you need to do is open the registry editor and search for the ms-msdt key as described in the video. If the entry is removed, access to the associated malicious code will be denied. However, it is recommended that you export a backup of the Kay to easily restore it after Microsoft provides a proper patch.
Digital marketing enthusiast and industry professional in Digital technologies, Technology News, Mobile phones, software, gadgets with vast experience in the tech industry, I have a keen interest in technology, News breaking.